Cloud
Design and delivery of quality solutions for e-Commerce, application integration, IoT, analytics, AI/ML engineering, or migration of existing systems at cloud scale
Artificial Intelligence and Machine Learning
AI engineering: data insights, OCR, entity projections, text analysis, and more
Applying MLOps to developing, training, and deploying of ML models
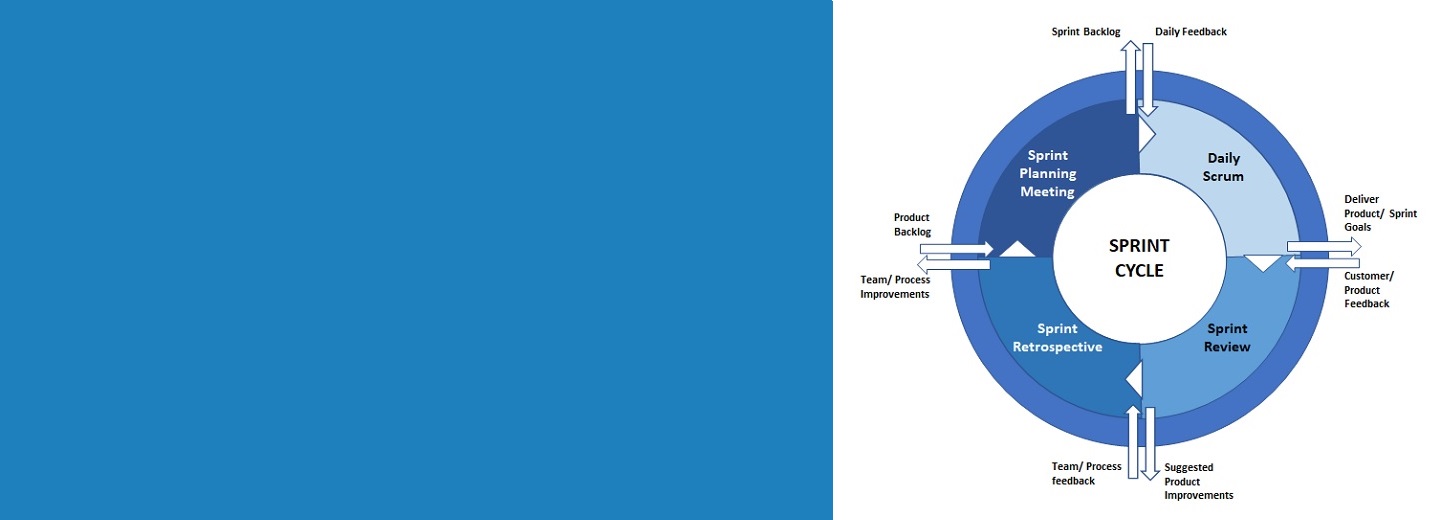
Agile and DevOps
Leading Scrum teams
Implementation of end-to-end DevOps
Security
Securing cloud resources, networks, applications, and data
Custom development with encryption and PKI
Cloud Solution Optimization
Optimizing solution performance, reliability, availability, scalability, and costs
Process Engineering and Automation
Engineering, optimizting, and automating business and development processes
Why Choose Us?
Integrity and Transparency
Quality by design is our purpose. We work with integrity in every aspect of our business. We are transparent with our customers in our analysis, design, and progress. The success of your project is our top priority.
Expertise and Experience
We have both breadth and depth of knowledge, skills, and experience across the entirety of application development lifecycle. The advanced skills and expertise in several key areas are backed up by multiple top industry certifications.
Certifications
-
-
 Azure Solutions Architect Expert
Azure Solutions Architect Expert
-
 Azure AI Engineer Associate
Azure AI Engineer Associate
-
 Microsoft Certified Solutions Expert: Cloud Platform and Infrastructure
Microsoft Certified Solutions Expert: Cloud Platform and Infrastructure
-
-

-
 Security+
Security+
-
-
-

-
 Professional Scrum Master
Professional Scrum Master
-
 Professional Scrum Developer
Professional Scrum Developer
-
-
-
 IBM Certified SOA Solution Designer
IBM Certified SOA Solution Designer
-
Object Oriented Analysis and Design (OOAD)
-